In my previous post, I wrote about how SSLMate has made my life easier.
I also mentioned how SSL-based attacks like POODLE and Heartbleed have forced us into using TLS.
Which is all very well, except that Microsoft’s whole premise in their product line is backward compatibility.
This means that a lot of older security protocols are on by default in Internet Information Service, even on Windows Server 2012 R2. As demonstrated by the recent vulnerabilities in the SSL protocol, this is not a good thing.
The recommended solution is to manually disable each of the older protocols using the registry editor.
IIS Crypto
Instead of this risky method, I discovered a free tool called IIS Crypto, by Nartac Software.
And so too, apparently, did @SwiftOnSecurity.
IIS Crypto is a free tool that allows configuring TLS protocols, ciphers, hashes and key exchange algos on WinServer https://www.nartac.com/Products/IISCrypto
This is how it looks:
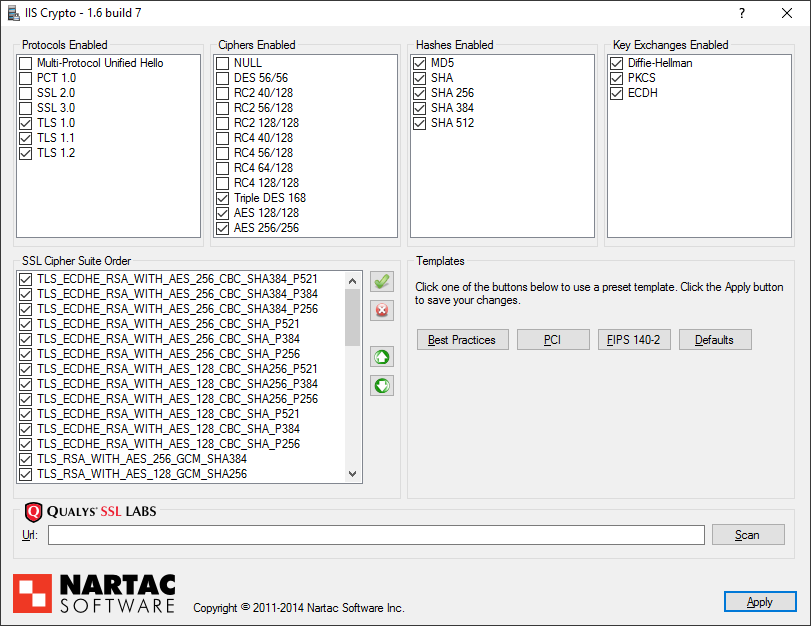
My recommended settings
I installed the .NET 4.0 GUI version. You can install the command-line version instead, but given that you’ll only run this application once or twice in the lifetime of the server, and you need to deselect some items, the GUI is easier to navigate.
Once you’ve installed IIS Crypto on your web server, run it and choose the Best Practices option (located under the Templates section).
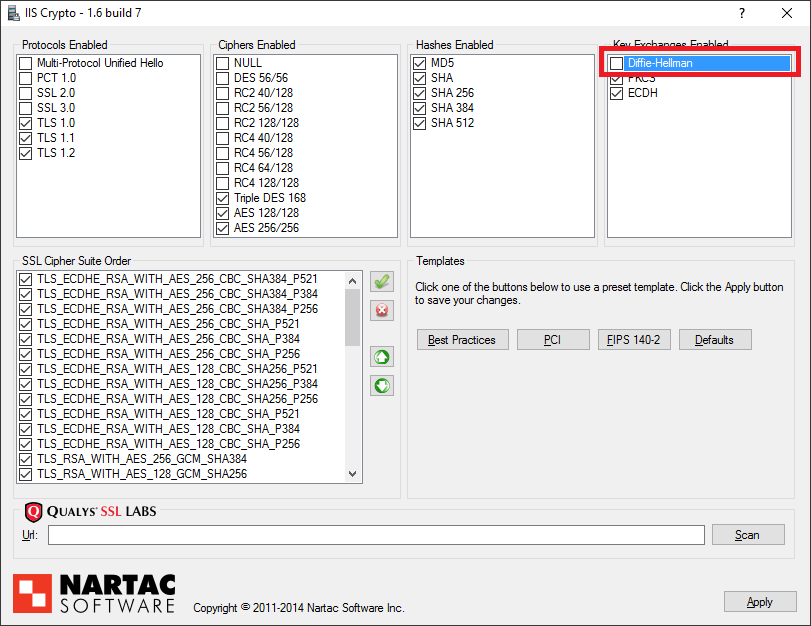
You will then need to uncheck the Diffie-Hellman Key Exchange, on the top right, like so:
Now you can click the Apply button, which will prompt you to restart your server.
In my own experimentation, I just issued an iisreset command to restart IIS, but it’s probably a good idea to restart the server anyway, as this tool makes changes to the Windows Registry.
Warning
According to the Qualys SSL Labs Test (which you can access from IIS Crypto in the URL field at the bottom of the screen), you will get a best score of an A-minus with these settings.
To achieve an A or higher, follow the instructions from the test result.
Coincidentally, because my company has more than one website served on the same IP address (common with virtual hosts), I achieved an A score by enabling SNI (Server Name Indication) on my website’s SSL bindings.
By default, this forces incompatibility with older browsers, who will be served a default SSL/TLS certificate, so keep this in mind.
Summary
I hope that this tool will make your life easier, by keeping only the most secure protocols and cyphers active on IIS.
This is just one aspect of security in depth. You should also look at the rest of the top 10 vulnerabilities, as collated by OWASP, to see how else you can protect your web applications.